News

DEF CON Hackers Uncover Voting Machine Vulnerab...
During the 2024 DEF CON hacking conference in Las Vegas, some of the nation’s most skilled cybersecurity experts gathered to probe the security of voting machines that will be...
DEF CON Hackers Uncover Voting Machine Vulnerab...
During the 2024 DEF CON hacking conference in Las Vegas, some of the nation’s most skilled cybersecurity experts gathered to probe the security of voting machines that will be...

Disney 1.2TB Slack Leak
An activist hacking group has claimed responsibility for leaking thousands of Disney’s internal messaging channels, which reportedly contain information about unreleased projects, raw images, computer codes, and some logins. Nullbulge,...
Disney 1.2TB Slack Leak
An activist hacking group has claimed responsibility for leaking thousands of Disney’s internal messaging channels, which reportedly contain information about unreleased projects, raw images, computer codes, and some logins. Nullbulge,...

What is a Pwnagotchi
Lets take a dive deep into what a Pwnagotchi is, how it works, and why it's become a beloved tool
What is a Pwnagotchi
Lets take a dive deep into what a Pwnagotchi is, how it works, and why it's become a beloved tool
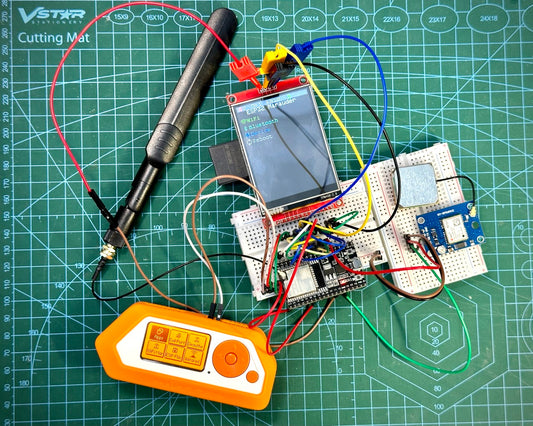
What is an ESP32 Marauder
In the ever-evolving world of cybersecurity and wireless technology, the ESP32 Marauder stands out as a versatile and powerful tool for both enthusiasts and professionals. Read more...
What is an ESP32 Marauder
In the ever-evolving world of cybersecurity and wireless technology, the ESP32 Marauder stands out as a versatile and powerful tool for both enthusiasts and professionals. Read more...

The 5 Most Notorious Hackers: Legends of the Cy...
Discover the legends of the cyberworld with the five most notorious hackers, including Kevin Mitnick, Adrian Lamo, Gary McKinnon, Albert Gonzalez, and Anonymous. Explore their impactful stories and how they've...
The 5 Most Notorious Hackers: Legends of the Cy...
Discover the legends of the cyberworld with the five most notorious hackers, including Kevin Mitnick, Adrian Lamo, Gary McKinnon, Albert Gonzalez, and Anonymous. Explore their impactful stories and how they've...

5 Huge Data Breaches: Unveiling the Digital Dis...
Discover the five largest data breaches in history, including Target, Equifax, Aadhaar, Marriott, and Yahoo. Learn about their massive impact on individuals and organizations in the interconnected digital world.
5 Huge Data Breaches: Unveiling the Digital Dis...
Discover the five largest data breaches in history, including Target, Equifax, Aadhaar, Marriott, and Yahoo. Learn about their massive impact on individuals and organizations in the interconnected digital world.
