Top 10 Hacking Tools Every Ethical Hacker Should Know
Share
Introduction
In today's digital age, ethical hacking has become a crucial aspect of cybersecurity. Ethical hackers, also known as white-hat hackers, play a vital role in identifying and mitigating security vulnerabilities. To perform their tasks efficiently, ethical hackers rely on various tools designed to assist in penetration testing, vulnerability assessment, and security analysis. Here are the top 10 hacking tools every ethical hacker should know.
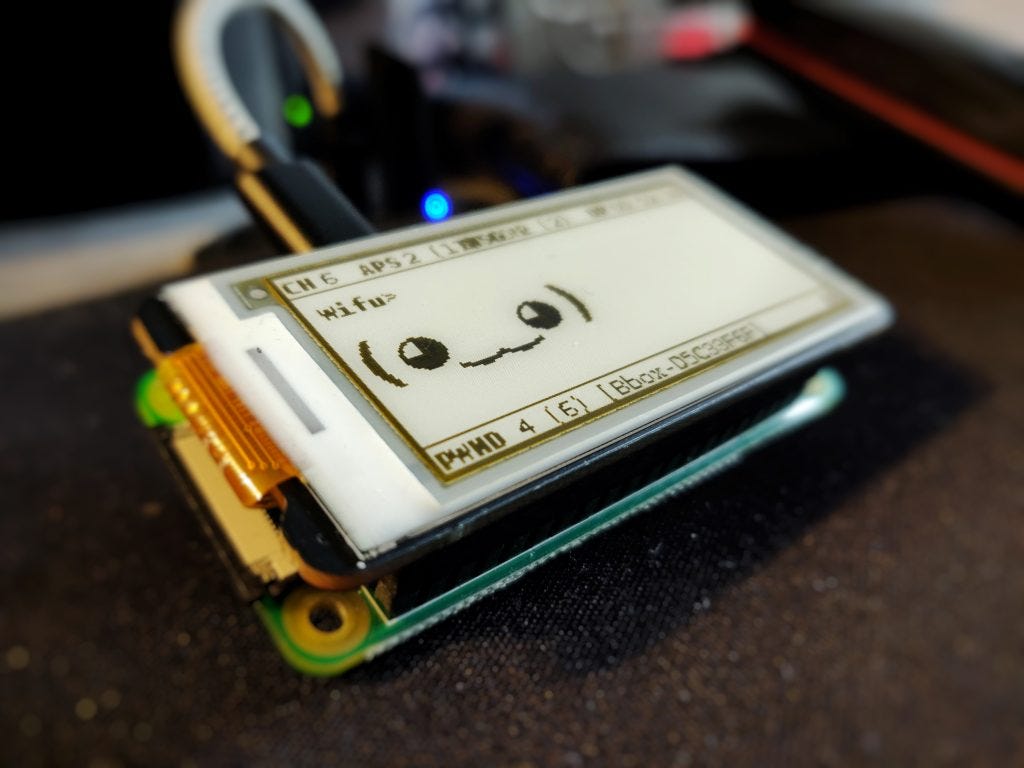
1. Nmap (Network Mapper)
Nmap is a powerful open-source network scanning tool used for network discovery and security auditing. It allows ethical hackers to discover hosts and services on a computer network, thus creating a "map" of the network. Nmap is highly versatile, offering a wide range of scanning options such as port scanning, OS detection, and version detection. Its ability to adapt to various scanning scenarios makes it an indispensable tool for network security assessments.
Key Features:
- Host discovery
- Port scanning
- Service version detection
- OS detection
- Scriptable interaction with the target
2. Metasploit Framework
The Metasploit Framework is one of the most popular and widely used penetration testing tools. It provides information about security vulnerabilities and aids in penetration testing and IDS signature development. Metasploit offers an extensive library of exploits and payloads, making it easier for ethical hackers to identify and exploit vulnerabilities in target systems.
Key Features:
- Exploit development
- Payload generation
- Post-exploitation modules
- Automated vulnerability scans
- Integration with other security tools
3. Wireshark
Wireshark is a network protocol analyzer that allows ethical hackers to capture and interactively browse the traffic running on a computer network. It is considered the de facto standard for network analysis, offering deep inspection of hundreds of protocols. Wireshark's capabilities make it an essential tool for diagnosing network issues and analyzing network traffic for signs of malicious activity.
Key Features:
- Deep inspection of hundreds of protocols
- Live capture and offline analysis
- Rich VoIP analysis
- Multi-platform support (Windows, macOS, Linux)
- User-friendly GUI
4. Burp Suite
Burp Suite is a comprehensive platform for web application security testing. It offers various tools that work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface to finding and exploiting security vulnerabilities. Burp Suite's modular approach allows ethical hackers to customize their testing environment according to their specific needs.
Key Features:
- Intercepting proxy
- Web vulnerability scanner
- Intruder (automated custom attacks)
- Repeater (manual testing)
- Extensibility through the BApp Store
5. John the Ripper
John the Ripper is a fast password cracker, primarily used to detect weak passwords. It combines several cracking modes in one program and is available for many different platforms. Ethical hackers use John the Ripper to test password strength and ensure that users' passwords are robust enough to resist attacks.
Key Features:
- Password cracking
- Support for various hash types
- Customizable cracking modes
- Open-source and community-supported
- Multi-platform support
6. Aircrack-ng
Aircrack-ng is a suite of tools for assessing WiFi network security. It focuses on monitoring, attacking, testing, and cracking WiFi networks. Ethical hackers use Aircrack-ng to capture and analyze packets, identify network vulnerabilities, and crack WEP and WPA-PSK keys.
Key Features:
- Packet capture and export of data to text files
- Packet injection
- WEP and WPA/WPA2-PSK cracking
- De-authentication attacks
- Real-time packet monitoring
7. SQLmap
SQLmap is an open-source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws. It provides a powerful testing engine and supports a wide range of databases. Ethical hackers use SQLmap to identify SQL injection vulnerabilities and take control of database servers.
Key Features:
- Automated SQL injection detection
- Database fingerprinting
- Data fetching from the database
- Accessing the underlying file system
- Executing commands on the operating system

8. Maltego
Maltego is an interactive data mining tool that performs link analysis and data visualization. It is used to gather information and perform analysis on relationships between people, groups, websites, domains, networks, and more. Ethical hackers use Maltego to map out the digital footprint of their targets and identify potential attack vectors.
Key Features:
- Graphical link analysis
- Data mining and information gathering
- Integration with various data sources
- Customizable transformations
- Comprehensive reporting
9. Nikto
Nikto is an open-source web server scanner that performs comprehensive tests against web servers for multiple items, including over 6,700 potentially dangerous files/CGIs, checks for outdated versions, and version-specific problems. Ethical hackers use Nikto to identify vulnerabilities in web servers and ensure they are secure against known threats.
Key Features:
- Scanning for potentially dangerous files and scripts
- Identification of outdated server components
- Checking for configuration issues
- Support for SSL
- Detailed reporting
10. Hydra
Hydra is a parallelized login cracker that supports numerous protocols to attack. Ethical hackers use Hydra to perform brute-force attacks on various services to test the strength of user passwords and ensure they are adequately protected.
Key Features:
- Support for numerous protocols (FTP, HTTP, Telnet, etc.)
- Parallelized and optimized for speed
- User-friendly command-line interface
- Extensive community support
- Customizable attack options
Conclusion
The tools mentioned above are essential for any ethical hacking toolkit. They provide a range of capabilities, from network scanning and vulnerability assessment to password cracking and web application testing. By mastering these tools, ethical hackers can effectively identify and mitigate security vulnerabilities, thereby contributing to a safer and more secure digital world.
As cybersecurity threats continue to evolve, ethical hackers must stay up-to-date with the latest tools and techniques. Continuous learning and practice are crucial for maintaining a high level of proficiency and effectiveness in the field of ethical hacking.
